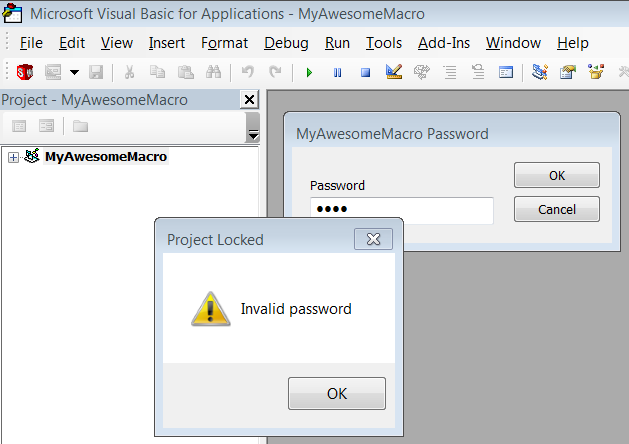
Any VBA macro, whether for SolidWorks or an Microsoft Office product, can have be locked using a password. The password is required to view the source code but not run the macro. This creates a neat little safeguard against tampering on the part of curious users, but it is not, in my opinion, a safeguard against piracy, for two reason. First, as mentioned, locking a macro doesn’t stop anyone from running it. Second, VBA macros can be easily cracked, as this blog post will demonstrate. If piracy is a concern, I recommend that you create your program as a .NET addin or stand-alone and use obfuscation alongside a password mechanism.
“Wait, so aren’t you just making piracy easier by documenting how to crack VBA macros?”
Doubtful. The steps I demonstrate here are simply adapted from StackOverflow posts explaining how to crack Excel VBA macros. Moreover, we have to keep in mind that just as a locked macro can be cracked for bad reasons, it can also be cracked for good reasons. For example, if the programmer leaves the company and the CAD manager needs to modify the macro, they will be forced to rewrite the macro or stop using unless they can access its source code. Therefore, my purpose in writing this post is two-fold:
1. Help those with legitimate reasons to access the source code to do so more quickly.
2. Highlight the insecurity of VBA macros, thereby encouraging programmers who want to protect their source code to use .NET addins or stand-alones instead.
How Macros Are Locked
SolidWorks VBA macros (.swp), as you probably know, are binary (non-text) files. If you open the .swp in Notepad, you’ll mostly see characters and symbols with no obvious meaning. The key word is “mostly” because if you look carefully, you will run into some metadata written in English that looks something like this:
CMG=”E1E34D8B518B518F558F55″
DPB=”5B59F77F6C9C6C9C93646D9C1EDAF1C91AF11C1729F7168075B76D9D66F46FEE731BC7DB9D”
GC=”D5D779F989728A728A72″
These three keys occur in two different places in the .swp, though I am not sure why. MSDN states exactly what these keys do. All three relate to the security mechanism, but, in particular, the DPB key contains the encrypted password. We don’t know what encryption algorithm Microsoft uses here and we don’t care. We just need to know that this is where the password is stored.
With Excel macros, it is sometimes necessary to modify all three keys (and sometimes in both places where they occur in the macro file), but the technique I am going to show you has worked for me when I modify only the first instance of the DPB key.
The Technique
1. Download and install HxD, which is a free and easy-to-use hex editor.
2. Create and save a new macro with a very short password, like the letter “a”.
3. Open this macro in HxD and search for “DPB”.
4. Copy the value of this key, as shown below.
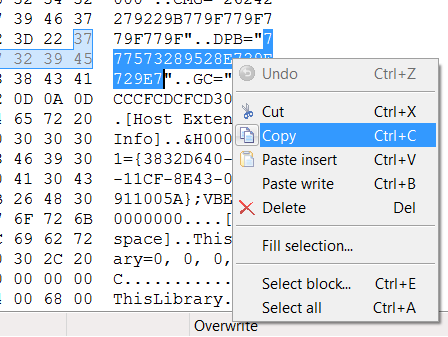
5. Open Notepad and paste the value in.
6. Repeat steps 3-5 with the macro with the unknown password.
7. Add zeroes on the end of the known macro password until it is the same length as the unknown macro password. For example:
Unknown Password
468BBA75C541A268B64FE75419213CC2311D94ECC09897A3F7A735980E
Known Password (with 4 extra zeroes added to end)
6B82387493970E5A40BBA0E25664D8D289FD0297D69DD881C85F6B0000
8. Back in HxD, replace the DPB key value for the unknown password with modified known password.
9. Save the macro in HxD.
You should now be able to unlock this macro in SolidWorks using the password from step 2. Don’t forget that you can remove the password entirely in the macro’s project properties.
If the above steps do not work, you can also try:
1. Replacing the DPB key in both places in the macro instead of just the first occurrence.
2. Replacing the CMG, DPB, and GC key instead of just the DPB key. I do not know whether identical lengths need to be maintained for CMG and GC, or whether it necessary to replace both instances.
Special thanks to Ivana K. for researching this technique.
Happy cracking,
Keith
Want to stay up-to-date with new CADSharp content, including new videos, blog posts, and training opportunities? Join our newsletter.

Your solution didn’t work for me. With OpenMcdf (https://sourceforge.net/projects/openmcdf/) I exported the PROJECT branch to an external file, edited that file like described above, replacing all three values, then imported the PROJECT back to the original, saved the macro file in OpenMcdf, and then opened that in SolidWorks with the known password.
The problem with your approach was that the keys (total keys length) were always longer than that of the protected macro.
Therefore, I had to increase the size of that part, and this could only be reliably made by the way I described.