Productivity Software and Tools That I Use

In this post I want to give you a peek inside how I organize myself as a software developer, software development team leader, and small business owner. Consequently, you’ll learn something not only about how I develop software but also how I run CADSharp. But before we get started, I want to make a few comments about productivity tools in general:
1. You will never find the perfect solution, so find something that works for you and just stick with it. The list of productivity and organizational tools is never-ending and many of them are largely redundant or only offer minute benefits over their competitors. Generally, you want to stick with tried and true options that obviously do not have an obvious overlap with your other tools.
2. Use a tool because it obviously makes you more productive / organized and for no other reason. If it is not clear to you how a tool might make you more productive or if the thought of using it stresses you out, don’t use it. It has taken me over five years to arrive at the point I am now. In some cases, I had to do something the inefficient way for years before it clicked in my mind how I ought to be doing it.
3. Don’t avoid a tool just because you’re afraid of the upfront work involved. This is the flip-side to the above: while you don’t want to force yourself into a workflow you’re not ready for, you could be hurting yourself by sticking with a workflow you know is inefficient. In my case, I balked at first of the hours it would take to migrate all of my prospective customers from Excel into Insightly (which I discuss below), but once I pulled the trigger it was a huge relief.
Now, onto the software and tools I use.
Visual Studio
Visual Studio Community Edition 2017 is the IDE (Integrated Development Environment) that I use to write code in. Yes, you can write .NET programs in any text editor, but no sane person would ever do this unless they’re either masochistic or trying to prove something to yourself to the world. Anyway, why do I use the Community Edition specifically instead of a paid editions (Professional and Enterprise)?
1. It is free for individual developers, open source development, classroom learning, or development teams of up to five developers working at organizations with less than $1 million in annual revenue. (Learn more about the limitations at the bottom of this link.)
2. It does everything I need and much more. Whereas the old Visual Studio Express Editions had limitations that were annoying to addin developers (since they required tedious workarounds), VSCE has very few limitations that are relevant to SolidWorks API developers. You can compare all of the editions here.
3. I prefer to use the same tools that my training students use. Since anyone can use VSCE for classroom learning, I prefer that all of my students are working with the exact same program I’m using to avoid any extra obstacles.
BitBucket
Think of BitBucket as the programming equivalent of SolidWorks PDM, except in the programming world, it’s not called “PDM” but “SCM” (Source Code Management). SCM lets you manage revisions and control code access. Where it gets confusing is that BitBucket isn’t source control itself (the SCM system I use is actually called Git) but rather a service that let’s you store your repositories online so that you can collaborate with your team or customers more easily. If you’re new to source control, it’s a bit confusing at first but soon becomes apparent how essential it is.
BitBucket has a famous competitor called GitHub. I use BitBucket because they allow free private repositories, whereas GitHub is only free for open-source (i.e., public) repositories. Beyond that, I can’t think of a reason I’m using BitBucket over GitHub. They both have great user interfaces, issue trackers, third-party tool integration, and everything else you could possibly want.
Alternatives: Microsoft’s SCM is called Team Foundation Server and their BitBucket / GitHub equivalent is called Visual Studio Team Services. These tools are integrated into Visual Studio. I have never used these tools so I can’t comment on their quality or ease of use for small development teams.
SourceTree
SourceTree is made by the same company that makes BitBucket (Atlassian) and is usually used in combination with BitBucket. I mentioned that BitBucket is an online tool for storing your code and collaborating with your team. Well, what about when you work on your code locally? How do you commit code (i.e., create revisions) in your local repository before its ready to push to your online repository? Well, Git (the name of source control system I use) lets you do all of that from the command line. Working from a command line, however, can be tedious. Enter SourceTree, which gives you a visual interface for common Git commands also a visual layout of your repository and its commit history. Is SourceTree necessary? No. Is it really useful? I think so.
Evernote
Evernote is a tool for remembering / storing information. Think of it as a database for text, images, and sound that you can easily organize and search. I use it to store lots of information about my business: code samples, programming tips, SolidWorks API technical support emails (that I copied and pasted into Evernote), the .NET guides I sell, blog post ideas, interview notes with prospective contractors, ideas for future projects, etc. Basically, anything that I would have kept in Word, Notepad, PDF, or email years ago. The problem is that searching for what you need is very difficult. You can’t search the contents of documents on your hard-drive en masse and working out of email is just annoying. Evernote solves this nicely: ALL of my infomation is in ONE place (though the information is still divided into separate notes) that is very easily searched. Moreover, if I need to share any of that information, I need only send the URL that links to that note.
Dropbox
Dropbox needs no introduction to most people, I would imagine. Even if you’re not familiar with Dropbox, you might be familiar with the competitors it produced like Google Drive and Box. I don’t have much experience with its competitors because Dropbox always satisfied my file-syncing needs. Basically, I use Evernote to store text information and Dropbox to store everything else: images, sounds, videos, source code, and other non-text documents. You might be thinking, “Wait a second — didn’t you say you store your source code online with BitBucket?” BitBucket is an online repository, but when I work with my source code locally, it’s still stored on a hard-drive. I keep all of my projects within Dropbox so I know that they’re being backed up online. Same for all of my business related files. If my computer got lost, stolen, or destroyed, I would need only re-download all of my files onto my new computer. Of course, my work files take up far more than the 2 GB provided by the basic account, so I do have Dropbox Plus, which gives me 1 TB for 99 USD per year. Note that Dropbox does have plans designed for teams and businesses. I do not use them since most of my collaboration involves source code and tools like BitBucket are far superior for that kind of collaboration.
Insightly
Insightly CRM (Customer Resource Management) is what I use to store customer informations, opportunities / leads, and ongoing projects. I chose it because it is free for up to two users and is pretty simple to use. If I do upgrade to the paid version it will mostly be to customize the data fields more extensively, since I use so few of the built-in fields and would prefer to create my own.
Slack
Slack lets you communicate with your team more effectively than via email. You can create a workspace for your company, invite people into that workspace, and give them access to public or private channels. For example, I and my contractors have a CADSharp workspace with a “general” channel that everyone has access to and private channels, named after customers, that only the contractors associated with those projects have accesss to. If I need to talk to a colleague about a project, I talk to them in that channel. That way we have a nice history of our conversation without cluttering our email inbox.
Trello
Trello is a task / project management tool that has effectively killed off my messy, tedious, and unenjoyable to-do lists of the past. For a long time I used Trello only occasionally or half-heartedly, but as my list of projects increases and my need for collaborating with colleagues increases, the value of Trello becomes more and more apparent. Trello let’s me invite colleagues into a “board” (which usually contains a To Do, Doing, and Done list) where I can assign them tasks, assign priorities and due dates to those tasks, attach files to those tasks, and write comments in the task’s comment section. Some of this could be accomplished via Slack, but Trello is designed more specifically for task management whereas Slack is designed more for general intra-company communication. You can integrate your Trello boards into Slack, however, and this is a avenue I might pursue in the future as my team becomes more comfortable with both tools. Aside from its simplicity, another reason I use Trello over its competitors is that Trello integrates very nicely into BitBucket, which allows me to attach commits, branches, and pull requests to Trello cards.
I didn’t list a particular email provider, because it doesn’t matter what email provider you’re using (or whether you’re using a web client or local client). Here’s what matters when it comes to email: You should only use email to communicate with people outside of your organization. In other words, you should NOT use email as a database, to-do list, or intra-company communication.
“But Gmail has such powerful search and organizational features!” It does. You can create folders, tags, etc, as can many other email providers. But if you’re using email like this then you’re using it as a database, which is not its purpose. Likewise, if you’re leaving messages unread (or marking them as unread) to create a rudimentary to-do list, you’re using email wrong. Why? Because other programs serve that purpose much better.
Once you have received information from the outside world, it should be immediately transferred to the appropriate place. In my case, that means my calendar if its a meeting or appointment, Evernote if its text information that I might need to look up later, Dropbox if its an attachment (e.g., SolidWorks models I need for testing a customer’s software), Trello if its a task, Insightly if I got the green light for a project, etc.
This is called “one touch” email philosophy: every email that comes into your inbox you touch once and then you should never have to worry about it again. This is why I don’t use email folders or tags or do anything at all with my emails after I read them (they just stay in my inbox forever): they serve no purpose in the one-touch system. That being said, I also don’t delete any non-trivial emails, in the event that I made a mistake in transmitting the data elsewhere.
As for intra-company communication: this one I’m not as passionate about, but in general I think that Slack or a tool like it is far superior for communicating with colleagues. As I state in my section on Slack: It greatly reduces inbox clutter, keeps conversations about specific projects in a more suitable place, and allows people to more easily ignore communication that isn’t relevant to them. (We’ve all been CC’ed on never-ending email chains that we couldn’t care less about.)
Of all of the advice and strategies I’ve shared here, adopting the one-touch philosophy has been the most difficult. I used email as a database and to-do list for so many years that it is hard to kick the habit.
Microsoft Office (Word and Excel)
Whereas some people have moved to Google Docs, I have not been inclined to do so for a few reasons. First, I prefer working out of desktop applications. Not because I’m “old-fashioned”, either. I just find working out a browser very unappealing not to mention I don’t like the feeling that I’m entirely dependent on an internet connection. Second, too many of my colleagues and customers still use Office products, particularly Excel. I don’t foresee Excel being replaced in many engineering workflows for the considerable future, which is why I have done numerous presentations on using the SolidWorks API and Excel API in tandem.
I also use Excel for my accounting needs. When I started CADSharp, I considered using Quickbooks or Peachtree but immediately realized that my accounting needs were simple enough that Excel would do the job just fine. To this day, therefore, I have a single Excel workbook that contains all of my balance sheets and ledgers. Until this business reaches the point where I can justify hiring an accountant, I’ll probably just stick with my current workflow since it’s so simple.
Online Meeting Software
I use Skype for one-on-one meetings with international colleagues and clients. The downside of Skype is that while you can share your screen, you can’t control someone else’s computer. For that you will need GoToMeeting, Webex, JoinMe, etc. If the customer doesn’t have their own service they prefer, I tend to use JoinMe, since it’s free.
Google Calendar
In my professional life, I mainly use Google Calendar to schedule meetings with customers. Perhaps it could be replaced by Trello or Slack for this purpose, but for the time being it serves me just fine and, since I have to use it for my personal life, anyway, I don’t have a strong desire to replace it.
Twitch.tv
Twitch.tv effectively lets any person create their own online television station. It’s mostly used by computer games who wish to stream themselves playing a particular game, but in recent years it’s become popular amongst artists and even software developers like myself. You may already know that I stream some of my work on Twitch. What you might not know is that I do this for productivity purposes more than marketing purposes. Yes, streaming does give me the opportunity to demonstrate my programming prowess to the world, but more importantly, it keeps me focused because I find it easier to stick to a task if I know people are watching me. I have also thoroughly enjoyed building relationships with the people who chat with me while I work. For those interested, I use Open Broadcaster Software to record myself while streaming.
Pandora
Pandora is a popular internet radio service that let’s you tailor stations according to your exact tastes. It’s also great for discovering new music. Spotify also accomplishes roughly the same thing, though it has more bells and whistles that I don’t care for. Anyway, I find that the right kind of music invigorates me while I work and therefore helps me stay focused. It helps push me through obstacles, you could say. If you’ve ever been on my Twitch.tv channel, you’ve probably heard me playing the station that I’ve spent the past five years tuning, which is an electic mix of electronica and instrumental, with a smattering of rock. Most of the songs do not have lyrics because I find lyrics distracting while working.
What productivity software could you or your team not live without? Please share in the comments below!
Productively,
Keith
Want to keep up with future content and training events? Sign up for our newsletter.
How to Crack A SolidWorks VBA Macro
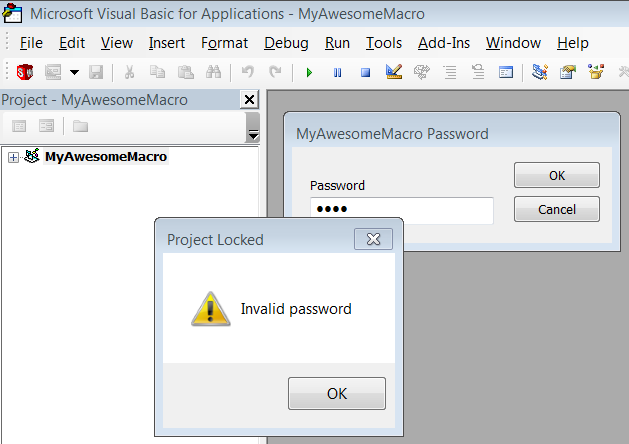
Any VBA macro, whether for SolidWorks or an Microsoft Office product, can have be locked using a password. The password is required to view the source code but not run the macro. This creates a neat little safeguard against tampering on the part of curious users, but it is not, in my opinion, a safeguard against piracy, for two reason. First, as mentioned, locking a macro doesn’t stop anyone from running it. Second, VBA macros can be easily cracked, as this blog post will demonstrate. If piracy is a concern, I recommend that you create your program as a .NET addin or stand-alone and use obfuscation alongside a password mechanism.
“Wait, so aren’t you just making piracy easier by documenting how to crack VBA macros?”
Doubtful. The steps I demonstrate here are simply adapted from StackOverflow posts explaining how to crack Excel VBA macros. Moreover, we have to keep in mind that just as a locked macro can be cracked for bad reasons, it can also be cracked for good reasons. For example, if the programmer leaves the company and the CAD manager needs to modify the macro, they will be forced to rewrite the macro or stop using unless they can access its source code. Therefore, my purpose in writing this post is two-fold:
1. Help those with legitimate reasons to access the source code to do so more quickly.
2. Highlight the insecurity of VBA macros, thereby encouraging programmers who want to protect their source code to use .NET addins or stand-alones instead.
How Macros Are Locked
SolidWorks VBA macros (.swp), as you probably know, are binary (non-text) files. If you open the .swp in Notepad, you’ll mostly see characters and symbols with no obvious meaning. The key word is “mostly” because if you look carefully, you will run into some metadata written in English that looks something like this:
CMG=”E1E34D8B518B518F558F55″
DPB=”5B59F77F6C9C6C9C93646D9C1EDAF1C91AF11C1729F7168075B76D9D66F46FEE731BC7DB9D”
GC=”D5D779F989728A728A72″
These three keys occur in two different places in the .swp, though I am not sure why. MSDN states exactly what these keys do. All three relate to the security mechanism, but, in particular, the DPB key contains the encrypted password. We don’t know what encryption algorithm Microsoft uses here and we don’t care. We just need to know that this is where the password is stored.
With Excel macros, it is sometimes necessary to modify all three keys (and sometimes in both places where they occur in the macro file), but the technique I am going to show you has worked for me when I modify only the first instance of the DPB key.
The Technique
1. Download and install HxD, which is a free and easy-to-use hex editor.
2. Create and save a new macro with a very short password, like the letter “a”.
3. Open this macro in HxD and search for “DPB”.
4. Copy the value of this key, as shown below.
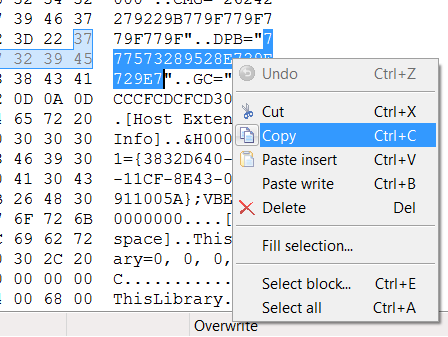
5. Open Notepad and paste the value in.
6. Repeat steps 3-5 with the macro with the unknown password.
7. Add zeroes on the end of the known macro password until it is the same length as the unknown macro password. For example:
Unknown Password
468BBA75C541A268B64FE75419213CC2311D94ECC09897A3F7A735980E
Known Password (with 4 extra zeroes added to end)
6B82387493970E5A40BBA0E25664D8D289FD0297D69DD881C85F6B0000
8. Back in HxD, replace the DPB key value for the unknown password with modified known password.
9. Save the macro in HxD.
You should now be able to unlock this macro in SolidWorks using the password from step 2. Don’t forget that you can remove the password entirely in the macro’s project properties.
If the above steps do not work, you can also try:
1. Replacing the DPB key in both places in the macro instead of just the first occurrence.
2. Replacing the CMG, DPB, and GC key instead of just the DPB key. I do not know whether identical lengths need to be maintained for CMG and GC, or whether it necessary to replace both instances.
Special thanks to Ivana K. for researching this technique.
Happy cracking,
Keith
Want to stay up-to-date with new CADSharp content, including new videos, blog posts, and training opportunities? Join our newsletter.
How to Protect Your .NET Source Code
Warning: I am not a software security expert. Please do not use this blog post as the basis for protecting highly sensitive code.
This past week I presented twice at SolidWorks World 2017 on SolidWorks API topics. In my first presentation, I demonstrated and discussed the pros and cons between macros, addins, and stand-alone programs as well as the common languages used to write each of them (VBA, VB.NET, and C#). One of the angles I considered was security. How can one protect their source code from being pirated or cracked? While this question isn’t about SolidWorks API per se, it is pondered often enough by API developers that I want to discuss it more detail.
Overview
With VBA macros, you only have one option: use the built-in password feature that will allow users to run the macro but not edit it. The problem is, this only stops people from viewing the source code. It does not stop anyone from using the macro. Moreover, with a little effort, one can replace the unknown password with a known password using a hex editor.
With .NET assemblies (e.g., the DLL or EXE that is built from your code), you have the option of implementing some form of licensing or password mechanism. This has two problems, however. First, as the licensing / password mechanism becomes more secure, it also tends to become more tedious for the user. (For example, if the licensing mechanism ties the user’s license to a particular machine.) Second, with some effort, the .NET assembly can be decompiled and then recompiled without the licensing mechanism.
While it isn’t possible to prevent decompilation (which is easily performed using a program like DotPeek and .NET Reflector), it is possible to obfuscate the source code in your assembly so that, even if it does get decompiled, understanding what your code does becomes difficult. Consequently, whatever security mechanism you have in place might be very tedious to remove.
Keep in mind: any client-side software can be pirated / cracked with enough time and effort. The only way to totally secure your source code is to never give your assemblies (i.e., your DLLs or EXEs) to anyone and instead use a Software-As-A-Service (SaaS) business model, in which case your assemblies will reside only on your server and your development machine. But SaaS isn’t even an option for many businesses.
A Change of Attitude
Trying to constantly stay one step ahead of pirates is usually futile. As one person on StackOverflow brilliantly put it, “It only takes one person cracking your code for it to be available to everyone. You have to be lucky every time. The pirates only have to be lucky once.”
More than just being futile, however, it can actually be bad for your business. The time and effort you put into securing your code does nothing to actually improve the user’s experience with your software. Indeed, if your security measures are cumbersome for the user to jump through, it can actually hurt their experience.
Consequently, the best deterrent to piracy may be to regularly improve your software and provide awesome customer service. As a result, the potential customer sees that the value you provide is worth the price they pay. They must believe that they will actually lose out by simply going with a pirated version of your software.
Another point to keep in mind is that if you’re selling business-to-business, the people who are going to use pirated copies of your software probably would not buy your software even if it were un-crackable. Therefore, I’m not convinced that in the B2B sphere, piracy actually results in that much loss of sales. If anything, piracy helps spread the word regarding your product and encourages you to focus harder on running a great business.
Anti-Piracy Measures Considered
Now, just because I think attitude is the most important measure you can take against piracy doesn’t mean its the only measure I think you should take. I think any program worth protecting ought to take these two measures:
- Licensing or password protection.
- Obfuscation.
Licensing / password protection simply means that your program requires some license key or password in order to operate. That way, pirates can’t simply copy your program and run it without any restrictions. But here’s the interesting part: the complexity or robustness of this mechanism is meaningless if pirates can simply decompile your program, remove the security mechanism, and then recompile it. This is always the case for programs given to the client. For example, consider this VB.NET program:
Imports System.Windows.Forms
Module Main
Sub Main()
Dim password As String = InputBox("Please enter the password.")
If VerifyPassword(password) Then
DoTheWork()
Else
MessageBox.Show("Sorry, wrong password.")
End If
End Sub
Private Function VerifyPassword(password As String) As Boolean
If password = "super secret password" Then
Return True
Else
Return False
End If
End Function
Private Sub DoTheWork()
MessageBox.Show("Running program...")
End Sub
End Module
The VerifyPassword() function is very simple. It tests to see if the user’s input string is identical to a hard-coded string. But what if this function was vastly more complex? It doesn’t matter because a pirate could simply decompile your code and modify Main() to include DoTheWork() and nothing else. The security mechanism would be completely bypassed.
Enter obfuscation. Obfuscation is “the action of making something obscure, unclear, or unintelligible”. We can use a code obfuscator to make our code very hard to read and understand by scrambling our code’s metadata so that the normal namespace, variable, and method names are replaced by extremely short and unhelpful names. You can see an example here. The result is simply that your code is much harder to reverse engineer.
Implementing the Anti-Piracy Measures
If you think that piracy could adversely affect your business, it is worth implementing some simple security measures to at least make piracy very tedious. I’m going to show you, therefore, the simple password mechanism and obfuscation tool I use with some of my programs. Look at these measures as the “biggest bang for your buck” because it will cost you nothing but 30-60 minutes of your time.
Password Mechanism
Earlier I showed a password mechanism in which the user simply enters a string and it is compared to a hardcoded string in the program. That’s a bit too simple and I think someone who decompiled our program could figure out pretty quickly what the password is. I would rather implement a password mechanism that is robust enough that the pirate is forced to modify and recompile our code if they want to bypass the security mechanism. (Again, my aim is to reduce piracy by making it tedious to do.)
We could get a little fancier with our string password using a cipher, which is an algorithm that will convert the user’s input password into something more cryptic. For example, let’s say that the password to our program is “hello”. Rather than hardcoding “hello”, we’ll hardcode “rcoeoqppvxlcvdkeyacd”, which was obtained by the following algorithm:
1. Convert each letter in the string to the 10th letter ahead of that letter. (“hello” –> “rovvy”)
2. Insert three random letters at the end of each of the letters obtained in the previous step.
The disadvantage of this approach is that the pirate could still take the time to study the algorithm after they decompiled the program and thereby discover that the password is “hello”. The pirate probably wouldn’t; they would probably just recompile the code without the security mechanism, but if we implement an even more robust password mechanism, we can at least force them to go the recompilation route.
The more robust mechanism I am thinking of involves the difficulty of factoring extremely large semiprimes. A semiprime is the product of two prime numbers. Currently, the technology for factoring a 1024 bit semiprime in a reasonable amount of time does not exist. Therefore, we will hardcode a very large semiprime into our program. The password the user enters will be divided into this semiprime. If the remainder is zero and the password entered isn’t the semiprime itself, one, or zero, then the program is unlocked.
What I described above is known as asymmetric or public key cryptography. It is the basis for most of the common encryption algorithms, such as RSA. When used, the pirate has no realistic way to determine the public key (the password), which means that they are forced to decompile, remove the security mechanism entirely, and then recompile if they want to pirate the software.
To accomplish this, we need to first generate some really large prime numbers. In our case, we’re interested in two 512 bit primes that we can multiply to get a 1024 bit semiprime. The fastest way to do this, I have found, is through WolframAlpha using the RandomPrime[2*512] function. Using this twice, I get these values:
1030036602598976432683876090384311619779817426568199635721909308334853846166282705348098491480965944058167494832551044953489873701037371663414513077893831
3470286731786319967697161150108216266467687635597343214439309083506091064461655902744916175294419695183449301769152696093634596665123123708757988896620687
We need to get the product of these two numbers. If you try to do this in .NET using double or ulong data types, you’ll run into problems because these types aren’t designed to handle numbers of this size. Instead we have to use System.Numerics.BigInteger class, which has methods for performing calculations with very large integers, such as BigInteger.Multiply(). Using that method for the above primes will produce this semiprime:
3574522355253486376607090679412058587605209637050288224651312594499415157606938016760090741648625564943457074837124758850059987557386762219300792006878464303045773124661517310657808537475286266496854670334149759621269093438046706289243962191687054489020476430544359972981836807607429766985418843679264281897
Now, below is what a simple program that uses one of the prime factors as a password would look like. Don’t forget to add a reference to System.Numerics.
Imports System.Numerics
Class Program
Private Shared Sub Main(args As String())
Dim enteredPassword As String = Console.ReadLine()
If VerifyPassword(enteredPassword) Then
Console.WriteLine("Correct password.")
Else
Console.WriteLine("Incorrect password.")
End If
Console.ReadKey()
End Sub
Private Shared Function VerifyPassword(enteredPassword As String) As Boolean
Dim semiprime As BigInteger = BigInteger.Parse("YOUR SEMIPRIME HERE")
If BigInteger.TryParse(enteredPassword, Nothing) = False Then Return False
Dim divisor As BigInteger = BigInteger.Parse(enteredPassword)
If divisor = semiprime Or divisor = 1 Or divisor = 0 Then Return False
Dim remainder As BigInteger
BigInteger.DivRem(semiprime, divisor, remainder)
If remainder = 0 Then Return True Else Return False
End Function
End Class
A few final considerations:
- A password mechanism can be used with DLLs as well. You can have an internal / Friend boolean variable called “unlocked”, for example, that must be true before the public functions in your DLL can be used.
- One advantage of the cipher approach over the factorization approach is that with a cipher you can allow for multiple possibly keys, and generate a separate key for each of your users. That way, if a key / password finds itself into the wild, you can at least trace it back to a particular user, for whatever that is worth.
Obfuscation
I’m going to show you how to use a free, open-source obfuscator called Obfuscar. It is not the most convenient obfuscator to use, nor is it especially powerful, but it is free. Check out Eazfuscator.NET and Dotfuscator if you want a more robust, paid obfuscator.
Obfuscar is obtained as as NuGet package. NuGet is a tool created by Microsoft that lets you easily add external libraries to your project. (It’s not used for necessity, but for convenience.)
- Open your project in Visual Studio
- Right click on the project that you want to obfuscate and choose Manage NuGet Packages
- Click Browse and search for Obfuscar
- Select it and click the Install button
- Create an XML file to your project folder called “obfuscar.xml” (technically, the name is arbitrary) with this text:
<?xml version='1.0'?>
<Obfuscator>
<Var name="InPath" value="PATH TO YOUR BUILD FOLDER" />
<Var name="OutPath" value="PATH TO YOUR BUILD FOLDER\Obfuscated" />
<Module file="$(InPath)\MyAddin.dll" />
</Obfuscator> - Edit the XML file to include your actual build folder (wherever the DLL / EXE is built to). If you have multiple DLLs / EXEs to build then you can have multiple Module nodes.
- Locate Obfuscar.Console.exe, which will be in a solution folder called “packages”.
- Run this executable from the command prompt with the path to obfuscar.xml as the argument.
- The obfuscated assembly will be located in your build folder in a subfolder called Obfuscated.
Note: Signed assemblies will not work after obfuscation with Obfuscar and must be resigned. Instructions on how to have Obfuscar sign your assembly post-obfuscation are here.
Additional Reading On Software Security
<> Obfuscating Code. Discusses the transparency of .NET assemblies and why obfuscation is essential for protecting software written in .NET.
<> Other ideas for protecting DLLs from being referenced: Here and here and here. The last one lists obfuscation and asymmetric cryptography as the first defenses and also explains the importance of focusing on building better software that customers want to pay for, versus obsessing over thwarting people who would never buy your software in the first place.
<> Security through obscurity – Is SolidWorks API-related code “safer” just because the SolidWorks API is not widely known of or used? It depends on what you’re trying to prevent. If you’re trying to prevent someone from using your assembly, no. If you’re trying to prevent someone from repurposing your code, probably.
Conclusion
Every developer has to consider the threat of piracy and then make a business decision on what amount of security is worth implementing. No client-side assembly can be completely safe, therefore it is important to know when “enough is enough”. Sometimes, the best anti-piracy measure is to add enough value through subscription or customer service that users aren’t tempted to use pirated versions of your software.
Most of the software I write is used internally by my customers, therefore piracy is not even on the radar. If you have experience writing software that is sold more publicly then I would be interested in your preferences regarding software security.
Keith
Want to stay up-to-date with new CADSharp content, including new videos, blog posts, and training opportunities? Join our newsletter.
